At the main program screen, the following options are available:
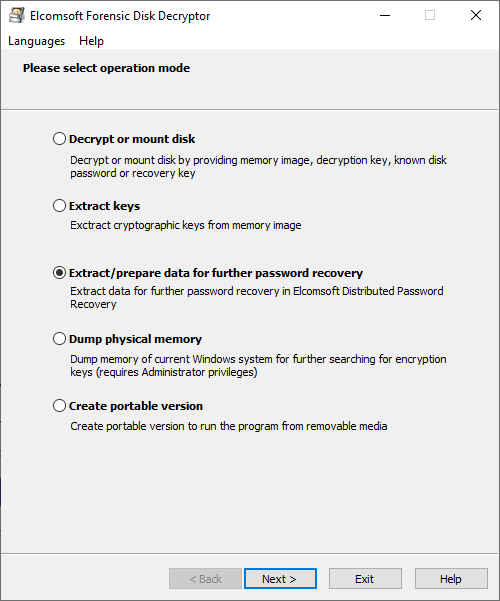
Decrypt or mount disk
See Decrypt or mount disk for details.
Extract keys
Once the disk is mounted into the system (unlocked), the system keeps the encryption keys in memory, and so can be extracted from there -- from memory dump (keep reading for more information how to get it) or from hibernation file (if the system has been hibernated while the disk was mounted). See Extract keys for more details.
Extract/prepare data
If password is not known, recovery keys are not available and there is not memory dump or hibernation file, then the only option left is recover the password using time-consuming brute-force or dictionary attack. EFDD allows to extract the data needed for further recovery; then you can use this data in Distributed Password Recovery for effective password cracking. Like with the first option (Decrypt/mount disk), select the data source first:
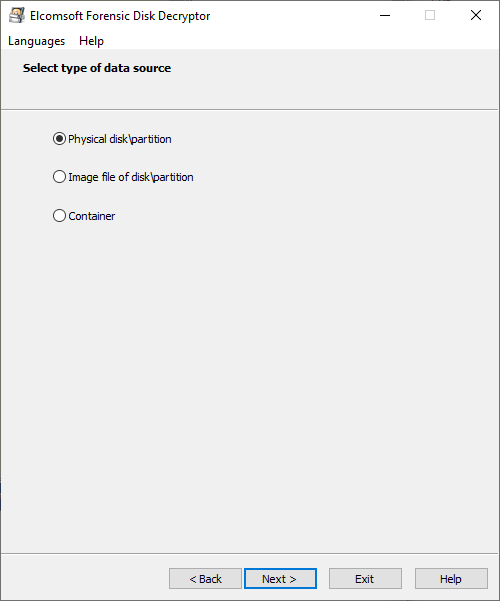
For the first two options, the program lists all partitions available and detects the encryption used there, if any. The last one (container) is for PGP (.pgd) and TrueCrypt/VeraCrypt containers (the latter may have any extension).
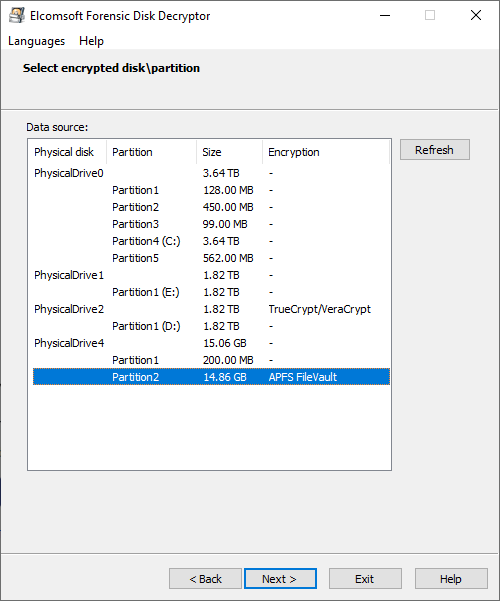
The data extracted with EFDD can be further used for password recovery with Distributed Password Recovery.
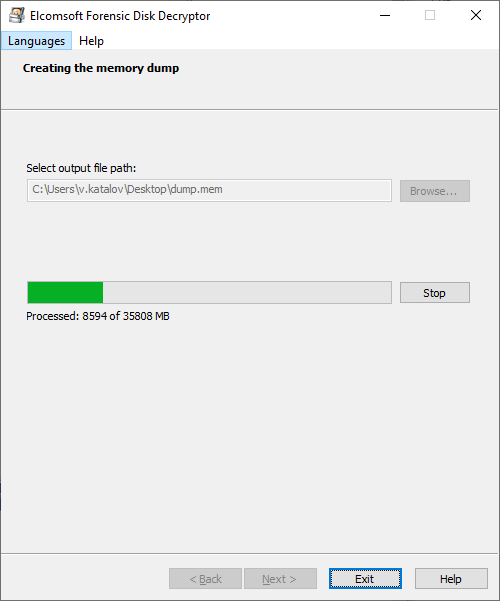
Dump physical memory
Once the disk is mounted into the system (unlocked), the system keeps the encryption keys in memory, so if you ahve access to the live system, the keys can be obtained easily. Select the file to dump memory to, and press Start; please bote that this operation requires Administrator privileges.
Create portable version
This option allows to create portable version of the program that can run from removable drive (on target's computer?). There are the following differences between normal and portable versions:
•portable version does not require installation; just run 'efdd.exe' to operate
•portable version dopes not include an option to create another portable version
•portable version cannot mount disks (just decrypt)