A Fully Integrated Solution for Accessing Encrypted Volumes
Elcomsoft Forensic Disk Decryptor offers a range of methods for gaining access to information stored in encrypted BitLocker, FileVault 2, LUKS, LUKS2, PGP Disk, TrueCrypt and VeraCrypt disks and volumes, and Jetico BestCrypt 9 containers. The toolkit allows using the volume's plain-text password, escrow or recovery keys, as well as the binary keys extracted from the computer’s memory image or hibernation file. FileVault 2 recovery keys can be extracted from iCloud with Elcomsoft Phone Breaker, while BitLocker recovery keys are available in Active Directory or in the user’s Microsoft Account.
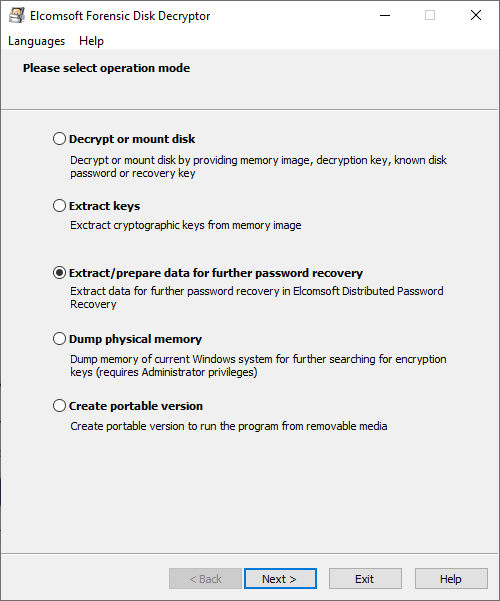
If neither the encryption key nor the recovery key can be extracted, EFDD can extract meta data from the encrypted container to let Elcomsoft Distributed Password Recovery do its job.
Extract Encryption Metadata
Extracting encryption metadata from the encrypted disk is required if you need access to the original plaintext password to access the data. Forensic Disk Decryptor will instantly extract the encryption metadata from encrypted hard drives, crypto-containers and forensic disk images protected with TrueCrypt, VeraCrypt, BitLocker, FileVault, PGP Disk, LUKS/LUKS2, and Jetico BestCrypt disks and containers. The resulting small file contains everything that's required to launch a GPU-accelerated distributed attack with Elcomsoft Distributed Password Recovery.
Full Decryption, Instant Mount or Attack
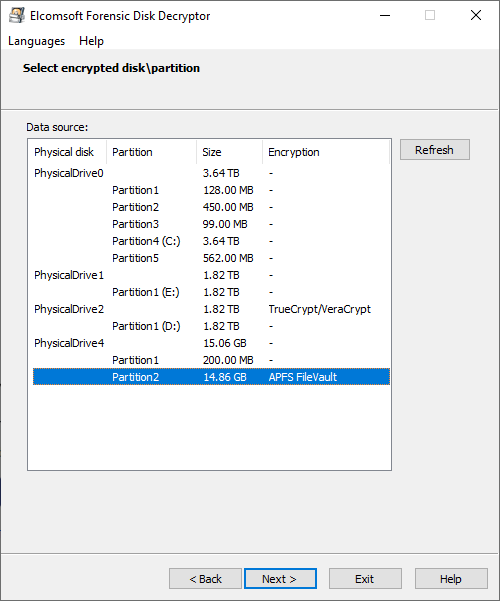
With fully automatic detection of encrypted volumes and encryption settings, experts will only need to provide path to the encrypted container or disk image. Elcomsoft Forensic Disk Decryptor will automatically search for, identify and display encrypted volumes and details of their corresponding encryption settings.
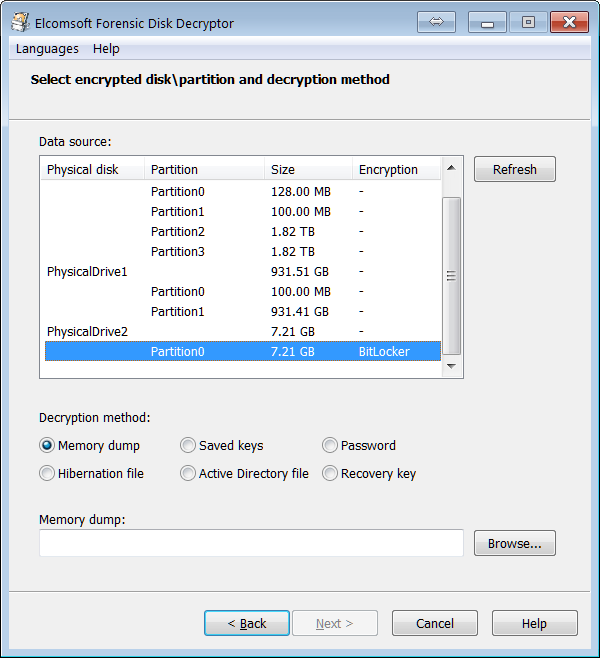
Access is provided by either decrypting the entire content of an encrypted volume or by mounting the volume as a drive letter in unlocked, unencrypted mode. Both operations can be done with volumes as attached disks (physical or logical) or raw images; for FileVault 2, PGP Disk and BitLocker, decryption and mounting can be performed using recovery key (if available).
Full Decryption
Elcomsoft Forensic Disk Decryptor can automatically decrypt the entire content of the encrypted container, providing investigators with full, unrestricted access to all information stored on encrypted volumes
Real-Time Access to Encrypted Information
In the real-time mode, Elcomsoft Forensic Disk Decryptor mounts the encrypted volume as a new drive letter on the investigator’s PC. In this mode, forensic specialists enjoy fast, real-time access to protected information. Information read from mounted disks and volumes is decrypted on-the-fly in real time.
No Decryption Key and No Recovery Key?
If neither the decryption key nor the recovery key is available, Elcomsoft Forensic Disk Decryptor will extract metadata necessary to brute-force the password with Elcomsoft Distributed Password Recovery.
Elcomsoft Distributed Password Recovery can attack plain-text passwords protecting the encrypted containers with a range of advanced attacks including dictionary, mask and permutation attacks in addition to brute-force.
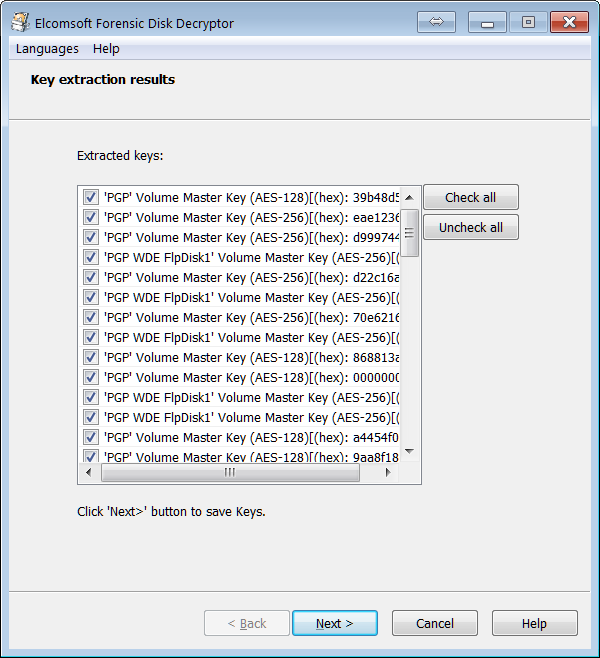
Sources of Encryption Keys
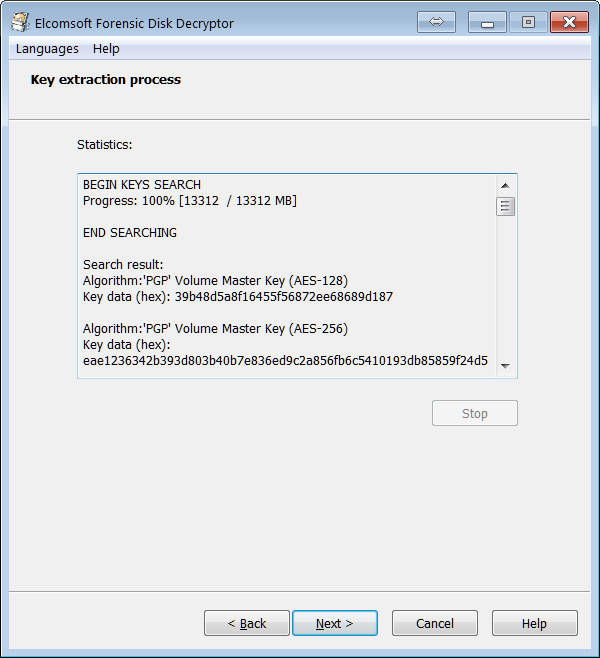
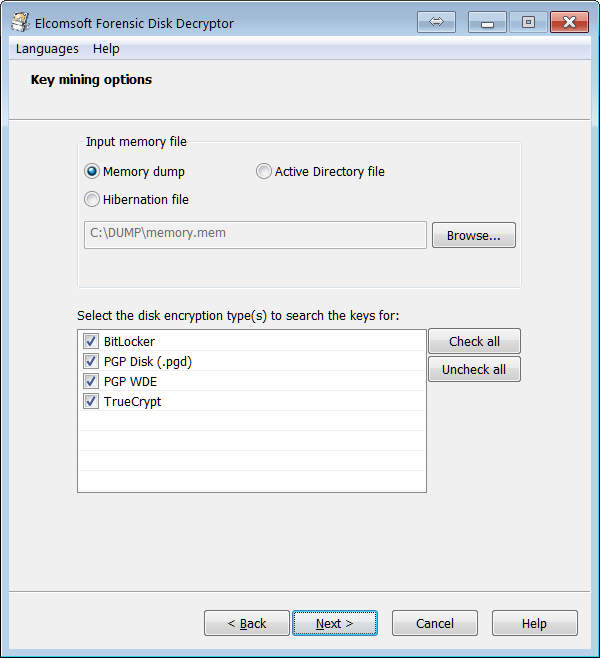
Elcomsoft Forensic Disk Decryptor needs the original encryption keys in order to access protected information stored in crypto containers. The encryption keys can be extracted from hibernation files or memory dump files acquired while the encrypted volume was mounted. There are three ways available to acquire the original encryption keys:
- By analyzing the hibernation file (if the PC being analyzed is turned off);
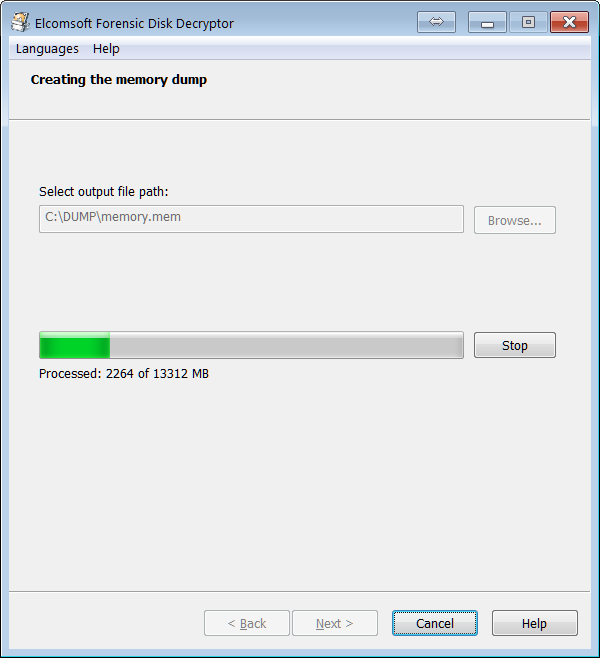
- By analyzing a memory dump file. A memory dump of a running PC can be acquired with the built-in memory imaging tool.
- By performing a FireWire attack (PC being analyzed must be running with encrypted volumes mounted). A free tool launched on investigator’s PC is required to perform the FireWire attack (e.g. Inception).
- By capturing a memory dump with built-in RAM imaging tool
FileVault 2, PGP Disk and BitLocker volumes can be decrypted or mounted by using the escrow key (Recovery Key).
Add more capabilities
Elcomsoft Encrypted Disk Hunter
Elcomsoft Encrypted Disk Hunter is a free, portable command-line tool to quickly discover the presence of encrypted volumes when performing live system analysis.
Multiple Windows, Linux and macOS full-disk encryption tools are supported including TrueCrypt/VeraCrypt, all versions of Microsoft BitLocker, PGP WDE, FileVault2, BestCrypt and LUKS. The tool must be launched with administrative privileges on the live system being analyzed. If an encrypted volume is detected, a further investigation of a live system might be needed to preserve evidence that could be lost if the computer were powered off.
» Read more about Elcomsoft Encrypted Disk Hunter in our blog