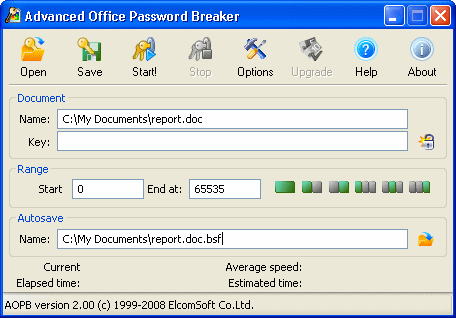
To break Word® or Excel® file that uses compatible encryption, open it in AOPB by pressing Open button on toolbar, and browsing for *.doc or *.xls file to be decrypted. The name of file will appear in the Document | Name input box. You can also use Open to load an existing project (*.bsf), which the attack has been partially completed for (to be explained later).
If you have Start the attack immediately after selecting document option enabled (see Options), this is all you have to do – the attack will be started with default parameters (sufficient for most cases), and now just wait till the key will be found (depending on the speed of your CPU, it may take from a few days and up to two weeks).
Please note that you can interrupt the attack at any time simply by pressing the Stop button. During the attack, the program saves (on a regular basis) intermediate information into the status file (with bsf extension). You can also save this file yourself at any point (using Save button on toolbar), or open previously saved file using Open button (instead of opening Word® or Excel® file here).
If Start the attack immediately after selecting document option is not checked, the parameters will be also set to default values, but you can change them prior to starting the attack. First, you can select an appropriate range. The whole key range (1,099,511,627,776 as defined above) is divided into 65,536 blocks, with 16,777,216 keys in every block. So Start from and End at fields may contain values from 0 to 65535; if you're just starting the attack, select minimum and maximum, accordingly. At the right of these fields, there are small buttons that allow selecting the whole range, or first/second half, or one third – this may help if you split the task across two or three computers. Next, you can select an alternatename for autosave file (with bsf extension).
Now press Start button on the toolbar, and the program will work till it find the encryption key or press the Stop button (you can do that at any time; the Start from field will be automatically set to the number of the current block). During the attack, the program shows some statistics – current block, average speed (in keys per second), elapsed time and estimated time.
Now you just have to be patient till the attack will complete so you will be able to decrypt your file – as already noted, it usually takes a few days (look at estimated time for more exact time) regardless the password length and complexity.
With the Enterprise version of AOPB, you can seriously speed-up this attack by enabling Use pre-computed hash tables option.
It is NOT recommended to use the tables directly from DVD (shipped with Enterprise version) because of very slow DVD drive performance. You can copy the DVD contents to the hard drive, or even better, to USB flash drive. USB flash drives have relatively low performance when reading files, but much better (than hard drive) random seek time, while this parameter is the most important for this attack.
With hash tables on hard drive, this attack takes from 10 to 30 minutes to complete; on USB flash drives – from just a few seconds and up to 10-15 minutes (worst case; usually much less: up to a minute). This option provides guaranteed recovery for Microsoft Word files, and about 97% success rate for Microsoft Excel files.