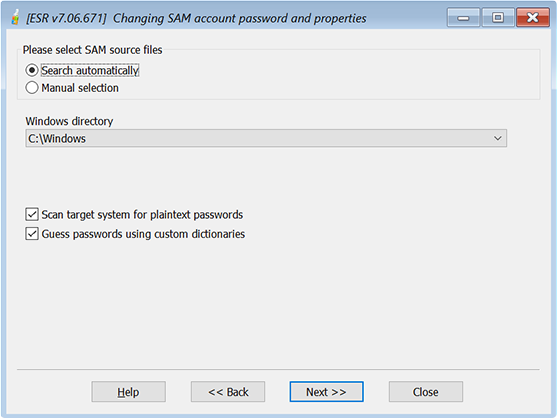
Once you selected a database source (SAM, DCC or AD) and working mode, you will be prompted to select the operating system to work with. If your system uses non-standard mass-storage adapters such as SCSI or SAS that are not supported by ESR, you may need to add drivers; see Mass-storage drivers for details. With the Auto selection, you can select the system folder from the drop-down box:
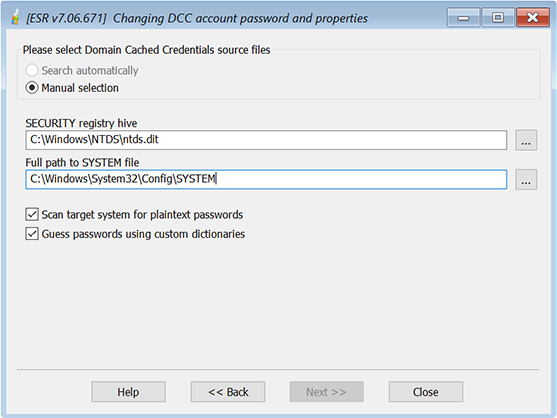
With Manual selection, you have to select the location of the AD database and SYSTEM Registry file using the [...] button at the right:
Alternatively, select the location of SAM, SECURITY and SYSTEM files:
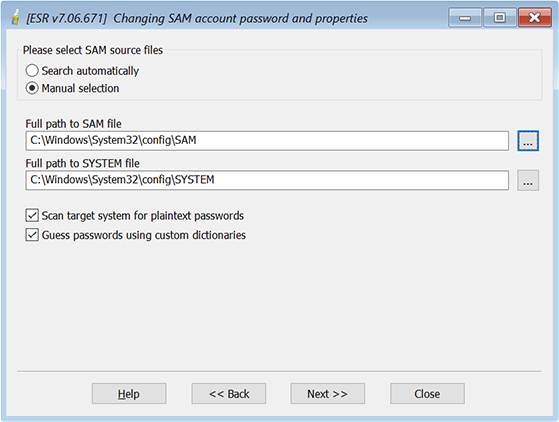
In manual mode, we recommend to select the location of the SYSTEM file first, so the location of SAM/SECURITY (or AD database) will be filled automatically. The default location of SAM, SECURITY and SYSTEM files is:
%WINDOWS%\SYSTEM32\CONFIG\
The AD database (ntds.dit) is usually stored in the following folder:
%WINDOWS%\NTDS\
If you don't see the local drives when browsing for SAM/SECURITY/SYSTEM/AD files, it can mean that you do not have the necessary drivers installed such as SerialATA, SCSI or RAID. You may need to specify them during boot process (see Booting from the CD or UFD for details).
If your system uses a non-default SYSKEY mode (i.e. SYSKEY is not stored in the Registry), then the program will prompt you for the startup password or SYSKEY floppy disk. If you do not supply them, password hashes cannot be extracted, and you will be unable to change account passwords or properties, or even dump password hashes into a text file.
If you selected the Test short and simple passwords option, ESR will try to recover passwords using several pre-defined dictionary and brute-force attacks. It will also attempt to decrypt passwords that could be stored or cached in other files. While this attack may not recover a lot of passwords, it only takes minutes and helps to recover short and simple passwords. These passwords will be tested:
•Obvious combinations such as passwords that are equal to login names
•Stored dial-up passwords
•Passwords from secrets (SECURITY registry file)
•Passwords from some browsers that can be decrypted instantly
•LM passwords
o4-characters (caps, digits, 16 symbols)
oPasswords from the wordlist
oPasswords from the wordlist with one digit at the end
•NTLM passwords
o4 characters (small, digits, 16 symbols)
o4 characters (small, caps)
o5 characters (small)
o5 characters (caps)
o7 characters (digits)
o3 characters (all symbols)
oPasswords from the wordlist
oRepeatable combinations (like '00000', 'aaa' etc)
oKeyboard combinations (like 'qwerty')
oKeyboard combinations on OEM layout
After that, the program creates a few different mutations for passwords that have been found at previous steps, and tries to apply them to all accounts.