On the main program screen, select the following:
•path to user keychain file (login.keychain or login.keychain-db)
•user's password (if set)
•path to system keychain file
•path to system key file
For more information how/where to get them, please consult Obtaining keychain files chapter.
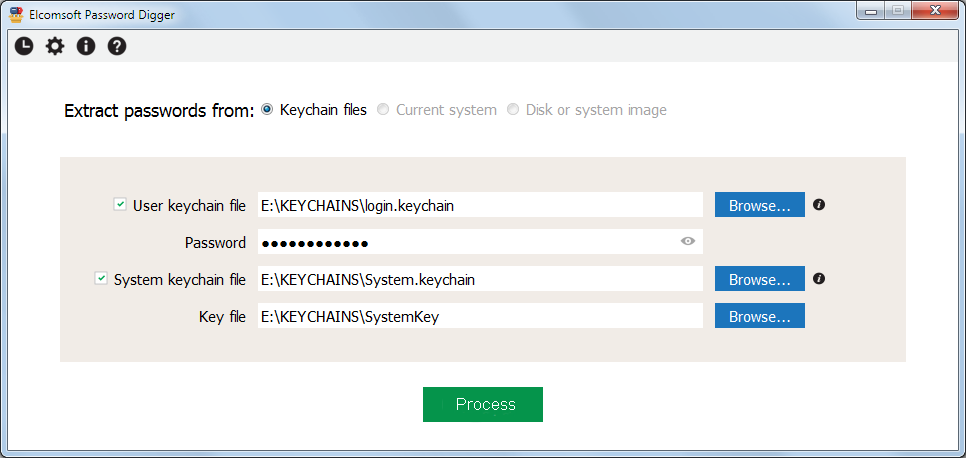
Once the files are selected (you can work with just the user's keychain, or system keychain, or both), please Process; if password is not correct, the program will not let you to proceed. The next screen shows how many records are processed in each file:
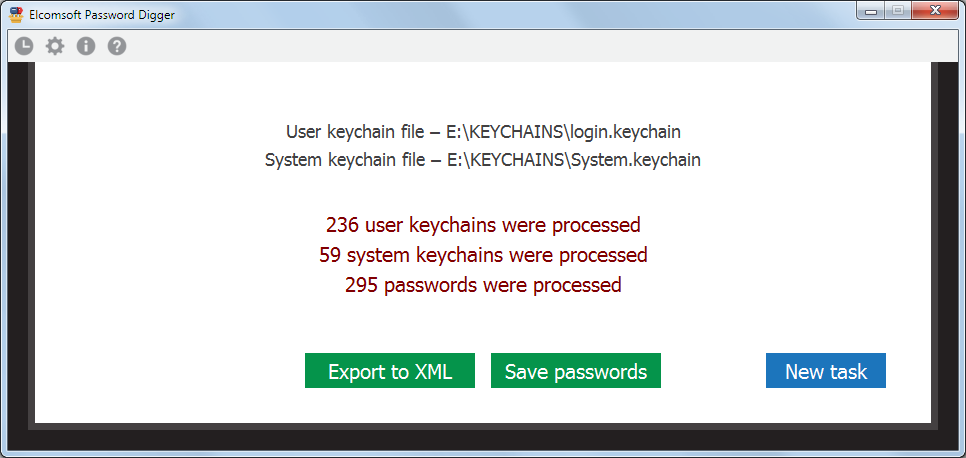
There you can export all records either to XML file (suitable for further analysis and/or reporting), or save just the passwords, so generating something like a dictionary/wordlist, e.g. to perform dictionary attacks with other software. The text file with password is sorted alphabetically (with the duplicates removed). XML file contains all the records from the keychains, including not just the passwords, but also the encryption keys, tokens etc, until you set the "Ignore non-password data in XML output" option.